Cloud Infrastructure Part III: Security
A look into the security ecosystem today, and where it will go from here
Cybersecurity remains one of the largest and most critical problems within software. Security solutions are what are known as tier 0 services, the highest level of criticality ascribed to third party software akin to cloud providers like AWS. Every company has a security “footprint” with varying degrees of complexity. A company typically has employees that work in various locations (offices, homes, factories, coffee shops) with access to devices (laptops, phones, tablets). These employees are likely siloed into distinct business units that each use their own software (R&D, marketing, finance, sales, HR) and share the same digital resources (Google Drive, a Postgres database, printers). What’s more - perhaps over half of their workforce will never come back into the office and are permanently remote.
On top of that, the cloud only exacerbates the problem. If companies have live applications or websites, then they are usually using a cloud provider like AWS or Azure on the backend to host and deploy their software. They’re also likely using out-of-the-box API services like Twilio and Stripe so that they can focus on selling their core product. Maybe they have some on-prem instances or VPCs. The growing use of the cloud creates gaps in security coverage and significantly increases attack surface areas.
At the same time, today’s cybersecurity threat landscape is more dangerous than ever. Data, devices, and applications are increasingly distributed and vulnerable to attacks ranging from weekend hackers to well-funded nation states. Breaches are highly deliberate and often executed in multiple, seemingly random steps. Consider the Log4j vulnerability last year that affected nearly 90% of IT environments. Or the SolarWinds breach that impacted 18,000 companies. These kinds of attacks won’t be the last.
But such a pervasive and important problem only begets incredible opportunity. Security markets are absolutely enormous: Gartner expects global security spend to exceed $170B in 2022. A recent Morgan Stanley report shows that even with the recent downturn, security remains the most defensible area of spending within IT budgets as CSOs work to secure an expanding threat environment. The business of protecting companies and their assets from malicious actors has produced generational businesses like Palo Alto Networks, Crowdstrike, and Zscaler. Even with the recent stock market correction, there are 8 cybersecurity businesses trading with a market cap greater than $10B today.
There are hundreds of different subcategories and solutions you’ve probably never heard of. But at its core, security is governed by four fundamental units: infrastructure, identity, applications, and data (thanks Danel for capturing this). All of the various acronyms you find in a Gartner breakdown (DLP, IoT, CSPM, CIEM, SASE, SAST, etc.) will eventually roll up into these mega categories. As a result, there is likely a $100B+ market-cap company in each of these four categories.
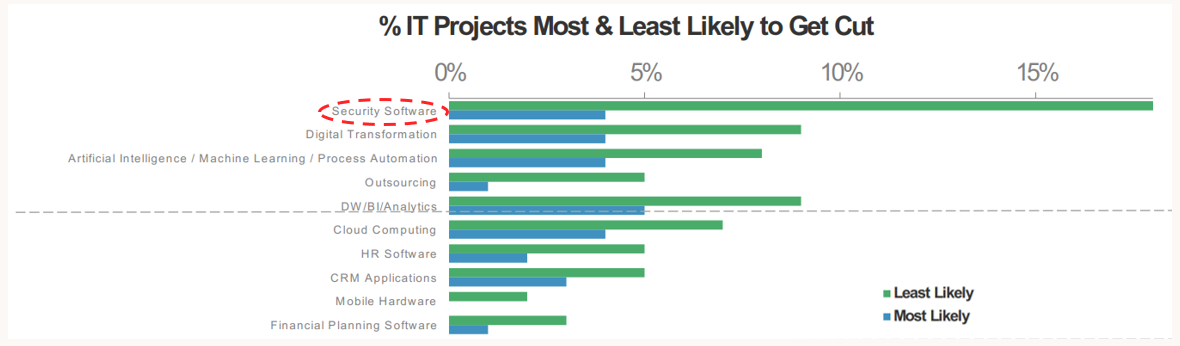
In my first post, I highlighted an emerging set of cybersecurity startups with recent funding that are pushing this category forward. Later on, we’ll see how CSOs are prioritizing these various solutions within their budget.
Key trends shaping this market:
1) Rise of agentless. Agentless security is a new, dynamic approach in which no code is deployed on workloads (container, VM, bare-metal server, etc.) to capture information related to the security of an environment. The advantages of agentless over agent-based include ease of deployment / maintenance and minimal performance impact (the more an agent monitors, the more resources it’ll consume). It’s also typically easier to get your IT team to approve a security solution that doesn’t deploy active agents in your corporate environment. Recent startups that employ an agentless approach include Cyera, Laminar, Orca, and Wiz.
2) Constant disruption within security. Security categories that were once thought of as the most entrenched and saturated are often prone to disruption. Take email security for example. For nearly two decades, everyone believed that the email security market wouldn’t change and that Proofpoint and Mimecast would always be the incumbents. But Abnormal Security flipped the status quo with its unique approach in using a knowledge graph + ML to detect email attacks that bypassed other providers. Within three years, it quickly became valued at $4B whereas Proofpoint and Mimecast were taken private by PE funds.
3) Increased cloud adoption creates gaps within security coverage. In 5 years, a quarter of all companies will have nearly all of their security workloads in the cloud. The shift to cloud significantly increases business risk and attack surface areas, as security policies that are typically applied within the traditional corporate network either cannot be enforced or are easily circumvented in a cloud environment.
4) Remote work brings new challenges. COVID-19 changed the way most businesses operate, creating a wide range of problems related to access and networking. The corporate network will eventually become irrelevant. Instead of relying on a firewall to protect your internal network from outside traffic, companies will focus on identity. Seamlessly understanding users and controlling what they can / cannot do will be the cornerstone of identity security. Recent startups tackling this problem include Axis Security, Tailscale, Teleport, and Twingate.
5) Developer-first security. As security “shifts left” and becomes more developer-centric, we will see the continued convergence of DevOps and security (aka DevSecOps). Developers and engineers will be both the users and buyers of security platforms. Snyk is a monster business in this category as it integrates security directly into development tools, workflows, and automation pipelines. They’re rumored to IPO soon. But there are a wave of startups like Chainguard and Legit Security that are addressing gaps within AppSec.
6) Humans continue to be the biggest threat. KnowBe4 is a ~$3B company selling security awareness training modules, which educate employees on security best practices. Fortinet is a massive $50B company just effectively selling firewalls. These solutions only exist because people often make mistakes that are prone to cyberattacks.
7) Becoming standalone. There is a no man’s land within security, where a cyber business stops growing and if lucky, is acquired by an incumbent like Palo Alto or Crowdstrike. The ones that get stuck in no man’s land are often “band-aid” solutions that don’t really solve a given problem. The ones that demonstrate and offer real IP tackling important problems are often characterized by quick time-to-value (where prospective customers can demo the real product in a fast POC), quick sales cycles, and high ACVs. These businesses have a real shot in breaking out and become standalone businesses.
8) Data security is the new cloud security. There are countless data security startups emerging today, and rightfully so. As data has exploded, companies are increasingly relying on new data infrastructure tooling to support their endeavors and adopting a new cloud data stack. As a result, managing data sprawl, PII, data loss, and associated data attacks is challenging. Startups like Cyberhaven, Cyera, Laminar, Normalyze, and Veza are innovating in this space.
The Security Budget
Budgets for security initiatives are sizable and remain a top priority for enterprises. We surveyed 60 CSOs in our network within organizations of 500+ FTEs, of which ~30% of respondents report paying $1M+ for 3rd party security. These CSOs plan to increase budget at a fair clip, with ~1/4 of security budgets to increase by at least 50% in the next decade.
When looking at where these dollars are being spent, I took a similar approach to my previous posts. To measure the priority of each subcategory relative to each other, I asked security leaders to rank order solutions by total dollars spent. I gave each respondent an imaginary budget of $2M to go spend on various security tools listed in the market map above. I asked everyone to do this now, and for the near future (5-10 years). It’s important to note that security practitioners weave together multiple vendors and components within their security architecture, as each is an important element within a broader security strategy. But not all categories are created equal, and spend is not distributed evenly.
With the tectonic shift to cloud-based security workloads, it’s no surprise that cloud security solutions like Orca and Wiz command the highest ACVs. Email security is a close second as 90% of attacks on organizations start from a malicious email. In third, we have AppSec companies like Snyk that help developers test for vulnerabilities during the build and release phases.
Where is Security Going?
Largest categories ($ spend) → Cloud security, email security, and AppSec solutions cement their positions at the top. SASE offerings will become more important as they replace traditional corporate VPNs and approach the networking problem from an identity-first standpoint. Data security rightfully remains in the top 5 as CSOs attempt to manage their accelerating data sprawl.
Fastest-growing categories (% inc. in spend) → Shifting left and developer-first security will be the fastest growing category over the next few years. In addition, it’s interesting to observe that common themes around identity (SASE, networking, identity orchestration) are top of mind for CSOs and will see continued investment moving forward. Data security, asset management, and cloud security offerings should see rising ACVs over the next 5-10 years.
Join Our Security Group
Similar to our data and infrastructure groups, we have an awesome advisory group of security practitioners at companies like Coinbase, Chainalysis, HashiCorp, and Snowflake. We host seminars, happy hours, and virtual events throughout the year. If you own security at your current company and would like to discuss new trends, up-and-coming startups, and meet other like-minded folks, please drop my colleague Chase Holmes or me a note. We would love to have you!